Resecurity | SharePoint Zero-Day Exploit (ToolShell)
Introduction
As reported by ISMG,
nearly 150 different organizations’ on-premises SharePoint servers have
been exploited by attackers targeting the zero-day vulnerabilities now
tracked as ToolShell. Early attacks have been attributed to China-linked
groups, in some cases leading to Warlock ransomware infections.
Resecurity observed in-the-wild exploitation activity as early as
July 17, 2025 prior to Microsoft’s official advisory. The attackers have
been chaining this vulnerability with previously patched flaws, CVE-2025-49704 and CVE-2025-49706, both of which were addressed in the July 8 Patch Tuesday release, with public PoC code emerging by July 14.
In addition to the technical exploitation, Microsoft has attributed the attacks to two named Chinese nation-state actors: Linen Typhoon and Violet Typhoon. Additionally, another Chinese threat actor, Storm-2603,
has also been linked to active exploitation. These groups have been
targeting internet-exposed SharePoint servers, with confirmed
compromises affecting a wide range of sectors including government
agencies, critical infrastructure, universities, and private enterprises
worldwide.
Leak from MAPP?
A security patch Microsoft released this month failed to fully fix a
critical flaw in the U.S. tech giant’s SharePoint server software,
opening the door to a sweeping global cyber espionage effort. Microsoft
is probing
whether a leak from its Microsoft Active Protections Program (MAPP)—an
early warning system for cybersecurity partners—may have enabled Chinese
hackers to exploit unpatched vulnerabilities in its SharePoint server
software. Microsoft confirmed that it “continually evaluates the
efficacy and security of all of our partner programs and makes the
necessary improvements as needed.”
The SharePoint vulnerability first came to light in May when Vietnamese security researcher Dinh Ho Anh Khoa demonstrated
it at the Pwn2Own cybersecurity conference in Berlin, organized by
Trend Micro’s Zero Day Initiative. Khoa was awarded $100,000, and
Microsoft issued an initial patch in July. However, Dustin Childs, head
of threat awareness at Trend Micro, said that MAPP partners had been
informed of the vulnerability across three waves – June 24, July 3, and July 7. Coincidentally, Microsoft noted the first exploit attempts began on July 7.
Childs suggested the most likely scenario is that “someone in the MAPP program used that information to create the exploits.”
While he didn’t name any vendor, he noted the exploit attempts
originated mostly from China, making it “reasonable to speculate” the
leak came from a company in that region.
The MAPP program, which debuted in 2008, was intended to provide
security vendors with advance notice of the technical details of
vulnerabilities — and, on occasion, sample proof-of-concept code — so
they could better protect their customers. A leaked breach now would fly
directly in the face of the program’s mission—empowering defenders, not
attackers. Microsoft has not disclosed whether it has identified the
source of the leak, but emphasized that any NDA breach would be taken
seriously.
Source of Active Exploitation
While the industry was focused on understanding the anatomy of the
attack, Resecurity’s HUNTER team was investigating the network
infrastructure associated with actors exploiting it at a very early
stage, leveraging the network passive sensors to collect relevant
telemetry to reproduce the origin of this malicious activity. Why is
this important? First of all, the notable detail is that the actors
successfully abused cloud infrastructure of multiple providers located
in different countries—including, but not limited to, the US, Brazil,
Germany, India, Hong Kong, Romania, the Netherlands, Taiwan, Japan,
Vietnam, and South Korea.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
July 17, 2025 – the IP 96.9.125[.]147
was detected as one of the hosts generating exploitation attempts. It
is not clear whether this activity could be related to a threat actor or
possible security researchers. The situation became clearer when the
exploitation shifted to a large-scale operation, involving IP addresses
from other regions.
This initial wave involved PowerShell-based payload delivery has been registered by Resecurity around July 18, 2025 (14:54–18:44 GMT) originating from 107.191.58[.]76. The
key differentiator what makes this activity different from previous –
dropping an actual malicious code, ASP-based web-shell designed for
Windows environment. A base64-encoded blob was decoded and written to
the SharePoint LAYOUTS directory:
$base64String = [REDACTED]
$destinationFile = “C:\PROGRA~1\COMMON~1\MICROS~1\WEBSER~1\16\TEMPLATE\LAYOUTS\spinstall0.aspx”
$decodedBytes = [System.Convert]::FromBase64String($base64String)
$decodedContent = [System.Text.Encoding]::UTF8.GetString($decodedBytes)
$decodedContent | Set-Content -Path $destinationFile -ErrorAction Stop
The resulting file, spinstall0.aspx, is not a traditional command webshell but rather a reconnaissance and persistence utility:
<%@ Import Namespace=”System.Diagnostics” %>
<%@ Import Namespace=”System.IO” %>
This
code extracts and prints the host’s MachineKey values, including the
ValidationKey, DecryptionKey, and cryptographic mode
settings—information critical for attackers seeking to maintain
persistent access across load-balanced SharePoint environments or to
forge authentication tokens.
What is interesting about this IP?

By the “Constant Company LLC” our investigators interpret the
following provider providing cloud infrastructure and GPU for rent:
Constant Company LLC is a parent company of Vultr, which specializes
in providing cloud infrastructure services. The company operates and
manages Vultr, offering cloud computing, bare metal, and virtual server
solutions to developers and businesses worldwide.
Notably, there was identified another cluster of IP addresses
involved in active exploitation originating from the same provider few
days later – July 21 and July 22. Likely, Chinese threat actors were abusing their cloud infrastructure to blur the origin of the attack.
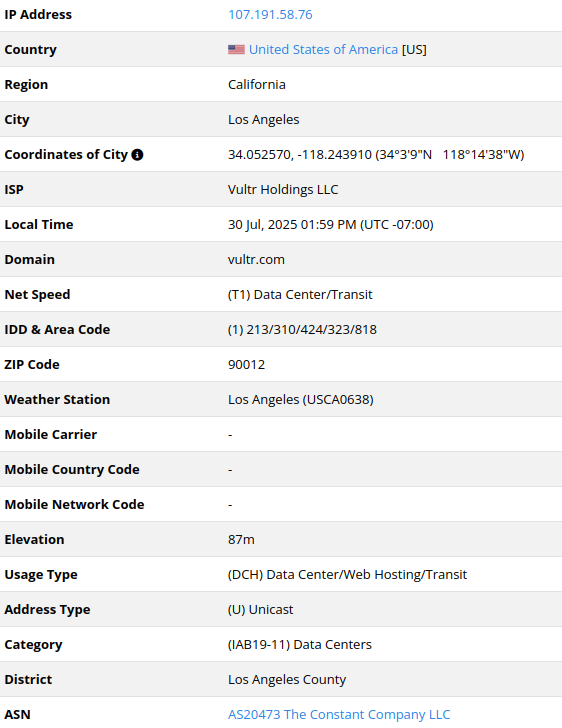
107.191.58[.]76
The Constant Company, LLC
2025-07-18
IP address exploiting SharePoint vulnerabilities.
64.176.50[.]109
The Constant Company, LLC
2025-07-21
IP address exploiting SharePoint vulnerabilities.
149.28.17[.]188
The Constant Company, LLC
2025-07-22
IP address exploiting SharePoint vulnerabilities.
Roughly 12 hours later, July 19, 2025 (03:06–07:59 GMT), a second wave used nearly identical logic to deliver the same spinstall0.aspx payload originating from 104.238.159[.]149. The key difference was in the PowerShell staging script:
$b = [REDACTED]
$c = “C:\PROGRA~1\COMMON~1\MICROS~1\WEBSER~1\15\TEMPLATE\LAYOUTS\spinstall0.aspx”
$d = [System.Convert]::FromBase64String($b)
$e = [System.Text.Encoding]::UTF8.GetString($d)
$e | Set-Content -Path $c -ErrorAction Stop
Start-Sleep -s 3
While
the encoded payload was marginally different in form, it decoded to the
same spinstall0.aspx shell. The change in target directory, from
16\TEMPLATE to 15\TEMPLATE, may reflect testing across different
SharePoint versions or environments. Unlike more interactive webshells
observed in this campaign, spinstall0.aspx does not support command
execution or file upload. Instead, its singular purpose appears to be
information gathering, specifically targeting cryptographic secrets that
could be reused to forge authentication or session tokens across
SharePoint instances. Given the uniqueness and strategic value of the
MachineKey data harvested by this shell, we assess this cluster to be
part of a broader effort to establish durable access into high-value
SharePoint deployments.
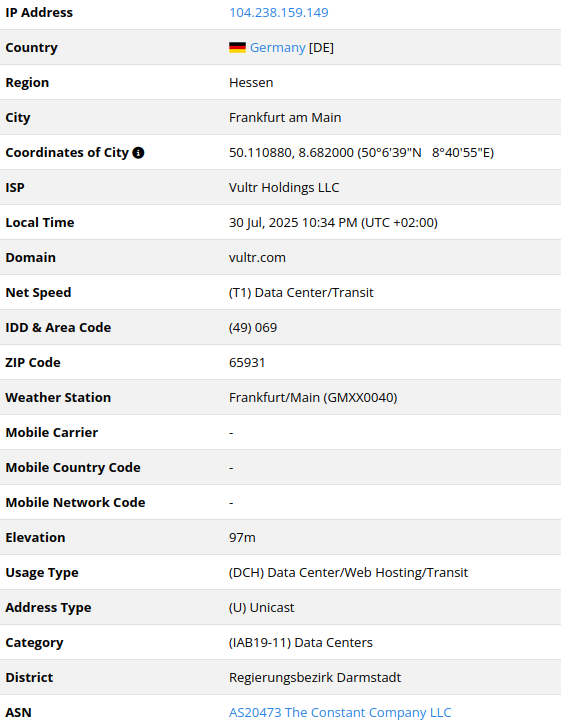
The exploitation efforts originated from three different IP addresses – 104.238.159[.]149, 107.191.58[.]76, and 96.9.125[.]147 – one of which was previously tied to the weaponization of security flaws in Ivanti Endpoint Manager Mobile (EPMM) appliances (CVE-2025-4427 and CVE-2025-4428).
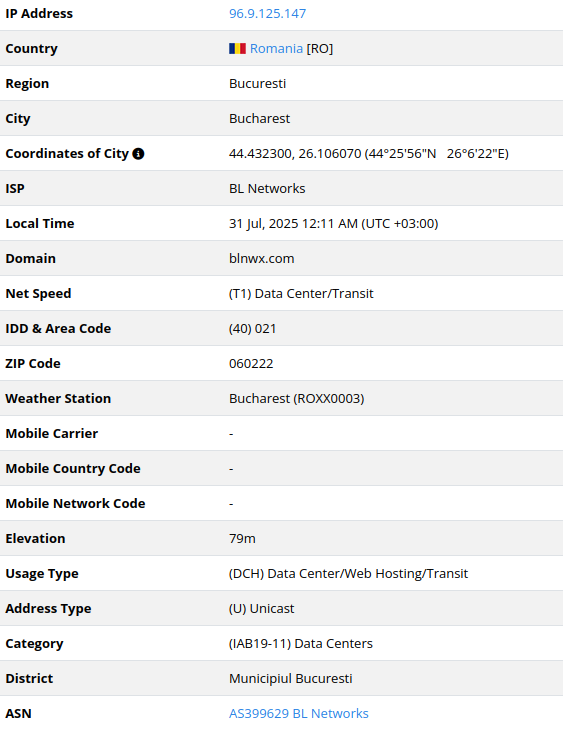
Notably, 96.9.125[.]147 was also mapped to a domain name “dynastyjusticecollective.site” registered around the same time the exploitation activity started, July 18:
WHOIS:
Domain Name: DYNASTYJUSTICECOLLECTIVE.SITE Registry Domain ID: D570923706-CNIC Registrar WHOIS Server: whois.namecheap.com Registrar URL: Updated Date: 2025-07-18T06:55:55.0Z Creation Date: 2025-07-18T06:55:51.0Z Registry Expiry Date: 2026-07-18T23:59:59.0Z Registrar: Namecheap Registrar IANA ID: 1068 Domain Status: serverTransferProhibited Domain Status: clientTransferProhibited Name Server: DNS1.REGISTRAR-SERVERS.COM Name Server: DNS2.REGISTRAR-SERVERS.COM DNSSEC: unsigned Registrar Abuse Contact Email: [email protected] Registrar Abuse Contact Phone: +1.9854014545
After that, threat actors moved to a new group of IP addresses:
83.136.182[.]237
Alina Gatsaniuk
2025-07-21
IP address exploiting SharePoint vulnerabilities.
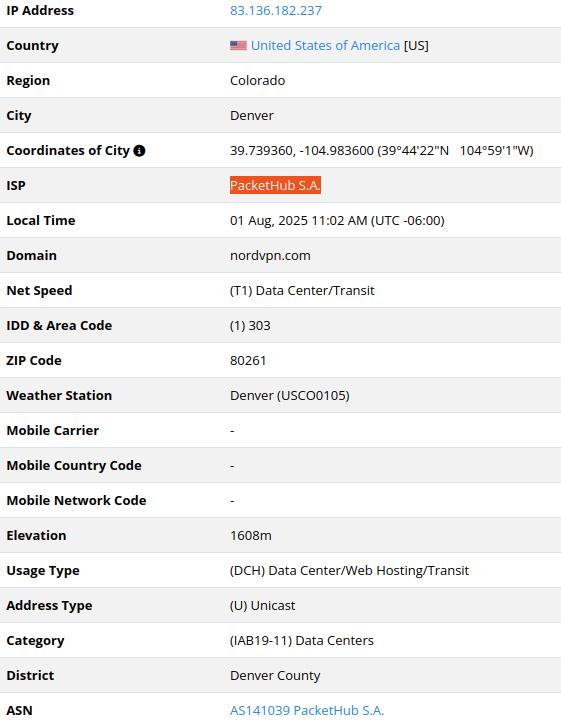
2.56.190[.]139
Alina Gatsaniuk
2025-07-22
IP address exploiting SharePoint vulnerabilities.
Deeper research may show that the network host is associated with the
UK-based connectivity, cloud hosting and dedicated servers provider Cloudvider. According to open sources, the name Alina Gatsaniuk was previously associated with NordVPN
and its related infrastructure. It is possible that the actors could
have leveraged VPN services during active exploitation or rented servers
through various third-party providers.
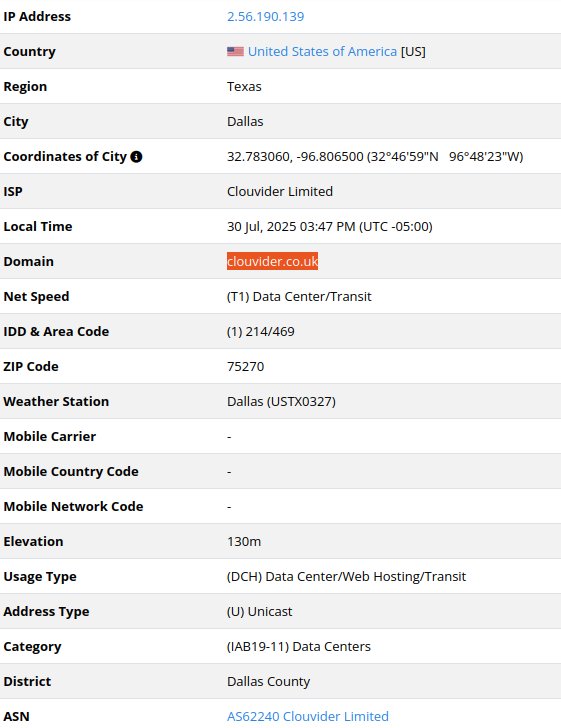
The identified IP is associated with one of such third-party providers with a relatively low-key profile, called Packethub, registered in Panama:
inetnum: 2.56.190.0 – 2.56.190.255
netname: PACKETHUB-20210602-DAL
descr: PACKETHUB-20210602-DAL
country: US
admin-c: AG25975-RIPE
tech-c: AG25975-RIPE
status: ASSIGNED PA
org: ORG-PS433-RIPE
mnt-by: CLOUVIDER-MNT
mnt-lower: CLOUVIDER-MNT
mnt-domains: CLOUVIDER-MNT
mnt-routes: CLOUVIDER-MNT
created: 2021-06-02T07:56:21Z
last-modified: 2021-10-28T10:52:58Z
source: RIPE
organisation: ORG-PS433-RIPE
org-name: Packethub S.A.
descr: Packethub S.A.
org-type: OTHER
address:
Packethub S.A., Office 76, Plaza 2000, 50 Street and Marbella,
Bella Vista, Panama City, 0823, Republic of Panama
abuse-c: PSAD2-RIPE
mnt-ref: CLOUVIDER-MNT
mnt-by: CLOUVIDER-MNT
created: 2021-10-28T10:46:09Z
last-modified: 2021-10-28T10:46:09Z
source: RIPE # Filtered
person: Alina Gatsaniuk
address:
Packethub S.A., Office 76, Plaza 2000, 50 Street and Marbella,
Bella Vista, Panama City, 0823, Republic of Panama
phone: +5078336503
nic-hdl: AG25975-RIPE
mnt-by: CLOUVIDER-MNT
created: 2021-10-28T10:49:40Z
last-modified: 2021-10-28T10:49:40Z
source: RIPE # Filtered
% Information related to ‘2.56.190.0/24AS62240’
route: 2.56.190.0/24
descr: Clouvider Limited
descr: DDOS mitigation route
origin: AS62240
mnt-by: CLOUVIDER-MNT
created: 2019-03-15T14:38:18Z
last-modified: 2019-03-15T14:38:18Z
source: RIPE
It is possible NordVPN utilizes PacketHub‘s infrastructure, including their IP addresses, for some of its servers. This means that when you connect to certain NordVPN servers, your traffic might appear to be coming from PacketHub. Multiple network intelligence and IP reputation databases flag PacketHub‘s
IP addresses as associated with NordVPN. Resecurity does not interpret
NordVPN or Packethub as being involved in malicious cyber activity, but
indicates that their infrastructure or services were likely abused by
attackers.
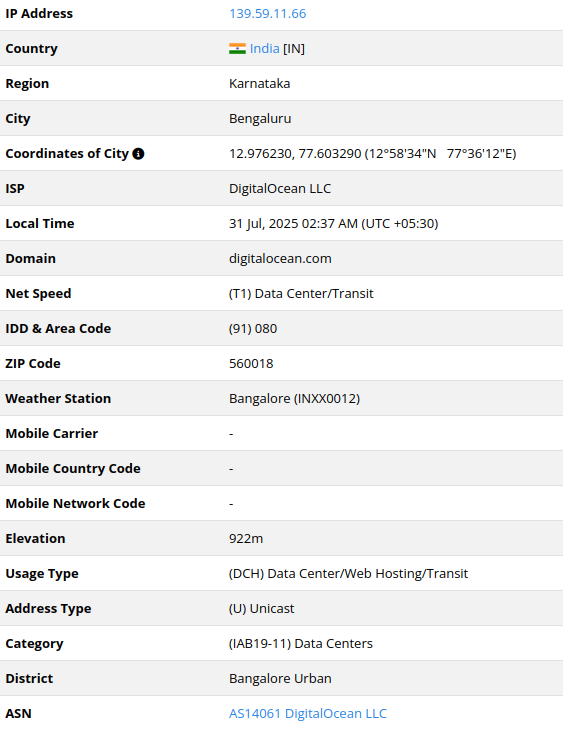
Another popular cloud provider – DigitalOcean – has
been abused during active exploitation. This IP had previously several
domain names mapped to it, primarily associated with Indian businesses
and personas. It is possible that threat actors abused it, compromised
the host, or registered their own VPS to conduct scanning.
139.59.11[.]66
2025-07-21
IP address exploiting SharePoint vulnerabilities
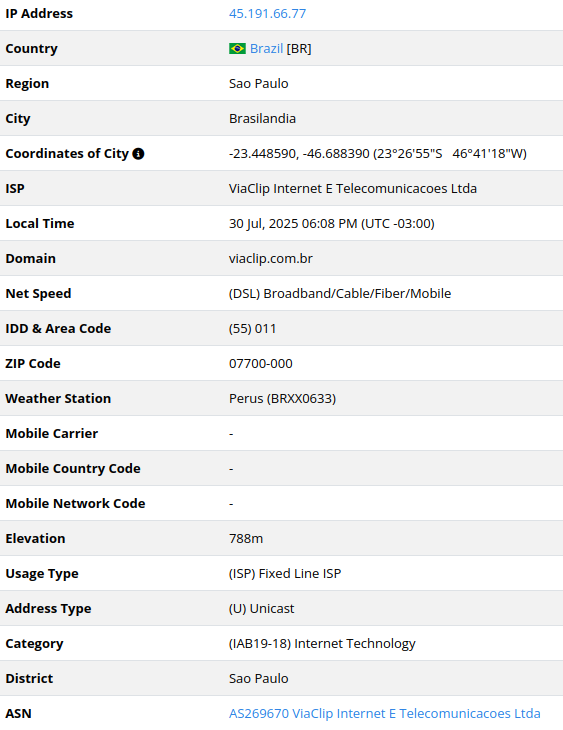
45.191.66[.]77
2025-07-21
IP address exploiting SharePoint vulnerabilities
45.191.66[.]77 – viaclip.com.br is associated with
VIACLIP INTERNET E TELECOMUNICAÇÕES LTDA, a Brazilian company that
operates as an internet service provider (ISP) and telecommunications
business. The company manages a small BGP (Border Gateway Protocol)
network and provides internet and telecom services in Brazil.
Other scanning IP addresses, including hosts from Europe and even
Asia-Pacific, allowed bad actors to obscure the origin of the attack.
Such tactics are expected when Chinese actors abuse the
telecommunication infrastructure of other countries and conduct
malicious cyber activities from third parties.
Due to the specifics of cloud services, the geographical resolution
of this activity may be fuzzy, as different providers registered in one
jurisdiction may have multiple rented or leased networks in other
locations, which can lead to misinterpretation of the sources of
attacks.
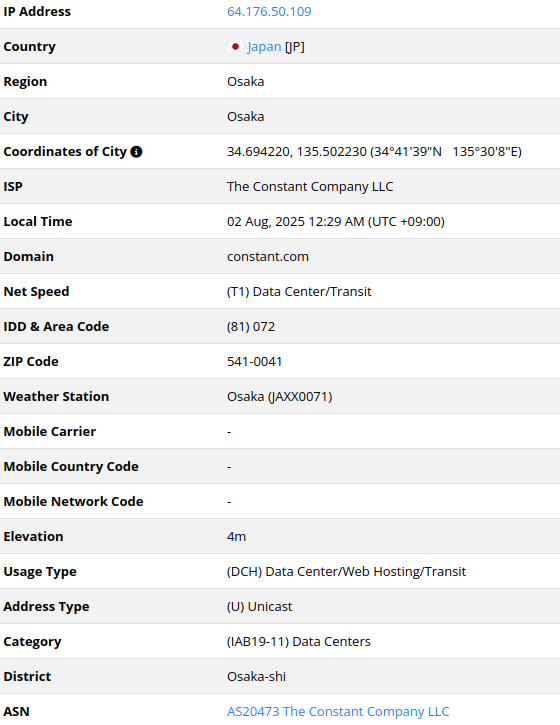
For example, some of the identified hosts used by attackers appeared
to originate from Japan, but in fact, they were tied to a US-based cloud
service provider.
64.176.50[.]109
2025-07-21
IP address exploiting SharePoint vulnerabilities
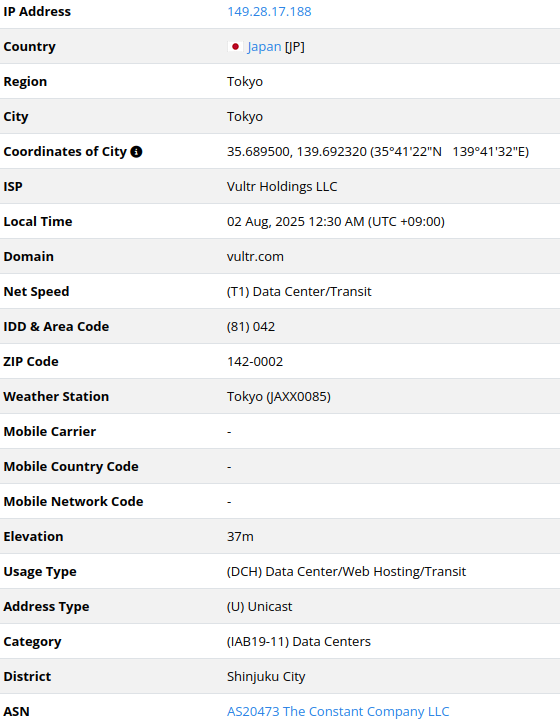
149.28.17[.]188
2025-07-22
IP address exploiting SharePoint vulnerabilities
162.248.74[.]92
2025-07-21
IP address exploiting SharePoint vulnerabilities
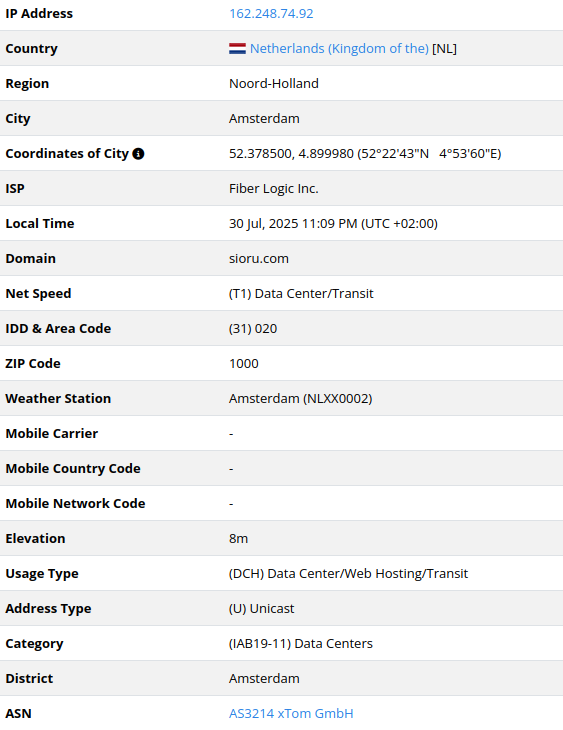
It is possible that Chinese actors aimed to leverage infrastructure
that would not indicate that the exploitation is originating from China.
That is why they were using several cloud providers outside of China
with a global footprint.
38.54.106[.]11
2025-07-21
IP address exploiting SharePoint vulnerabilities
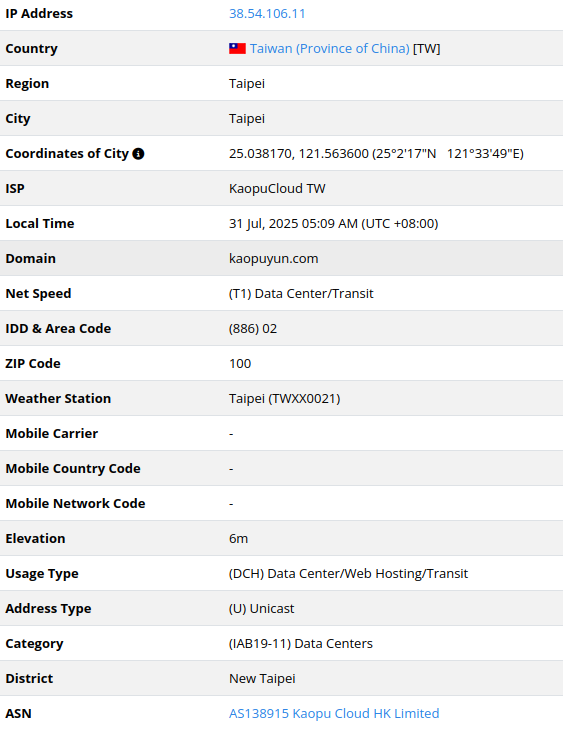
206.166.251[.]228
2025-07-21
IP address exploiting SharePoint vulnerabilities
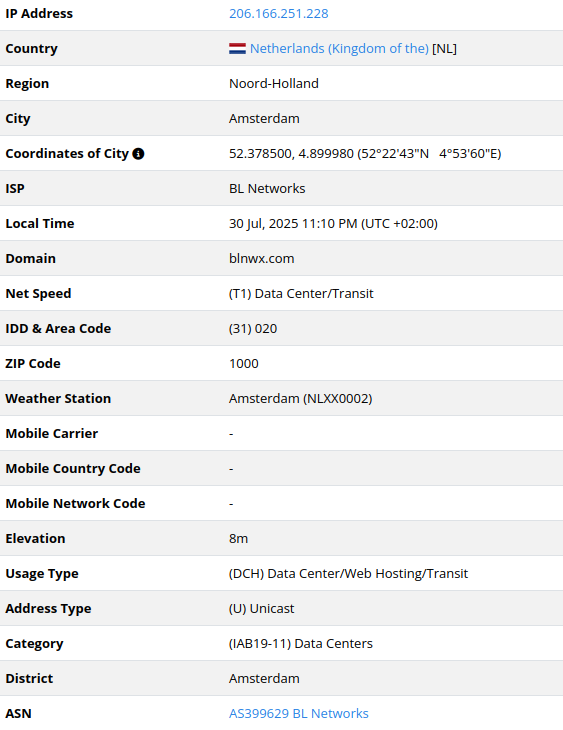
The web-site of this operator states: “BL Networks provides IP
addresses and related services to internet companies. BL Networks may
not necessarily be the direct operator of any equipment and/or service
currently or historically using a given IP address”.

45.77.155[.]170
2025-07-21
IP address exploiting SharePoint vulnerabilities
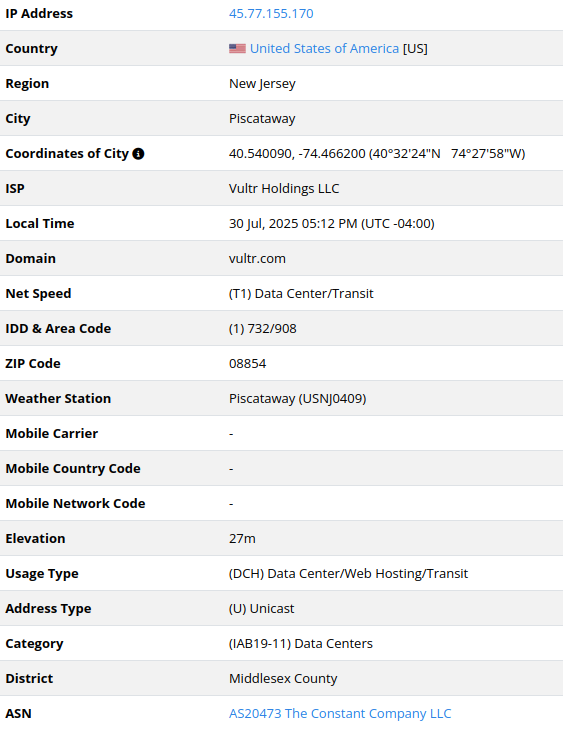
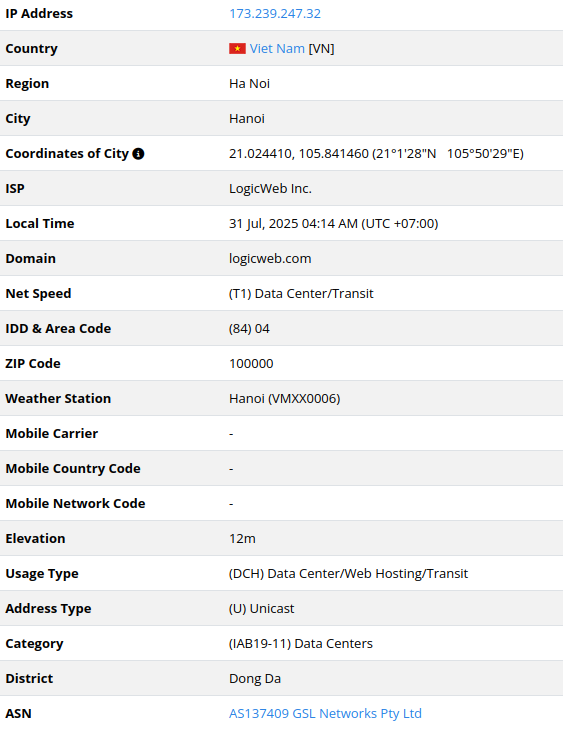
173.239.247.32
2025-07-22
IP address exploiting SharePoint vulnerabilities
173.239.247[.]32
– In fact, the IP is tied to LogicWeb Inc., operating out of the US.
The AS network associated with it is related to Australia-based AS137409
GSL Networks Pty Ltd, also known as Global Secure Layer (GSL), which
specializes in IP transit services and offers DDoS protection. According
to available network intelligence and IP reputation data, the IP may be
associated with a CyberGhost VPN server,
which could be used by cybercriminals for anonymization. It is common
for VPN services to rent cloud and dedicated servers from third parties;
in this case, this may lead to a mistaken assumption that the attack is
somehow connected to Vietnam due to fuzzy geographical resolution.
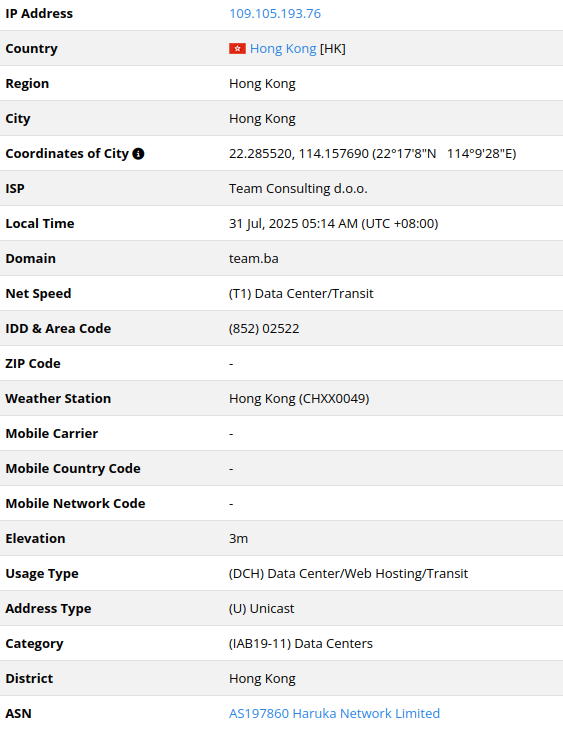
109.105.193[.]76
2025-07-22
IP address exploiting SharePoint vulnerabilities
109.105.193[.]76
– another good example of fuzzy resolution is that the IP address
information indicates the host could be managed by a company based in
Bosnia (Team Consulting d.o.o. Sarajevo).
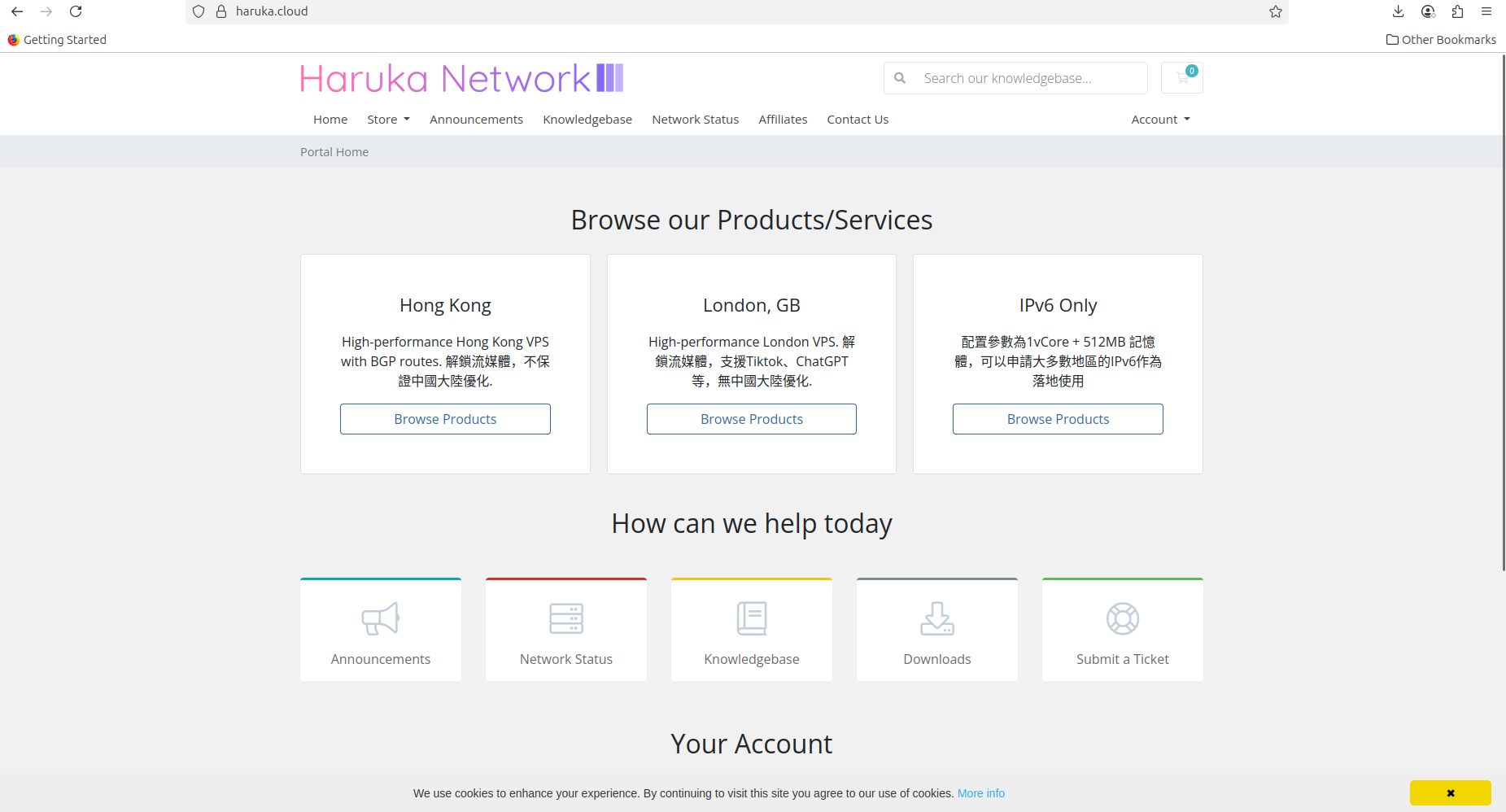
In fact, this IP block is tied to Haruka Hosting Ltd, associated with
Cenuta Dedicated Servers IP subnets (109.105.193.0/24). According to
Resecurity, “Haruka Hosting Ltd” is identified as a little-known cloud
provider with a legal entity in the UK registered under the name GAO,
Lingyu (Chinese national).
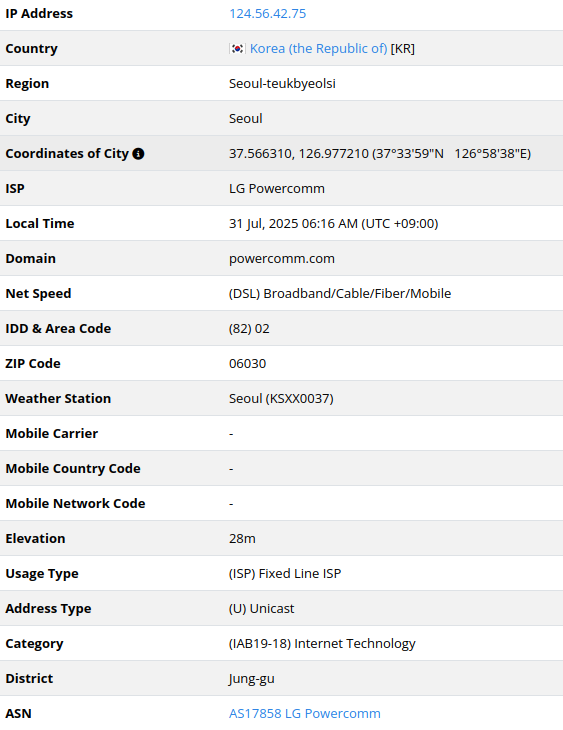
124.56.42[.]75
2025-07-22
IP address exploiting SharePoint vulnerabilities
124.56.42[.]75
– the host is tied to “Xpeed” in South Korea, an internet service
offered by LG POWERCOMM, a South Korean company. Specifically, LG
POWERCOMM enhanced its “Xpeed Optic LAN” service, upgrading internet
lines in apartment complexes from 100 Mbps to 1 Gbps.
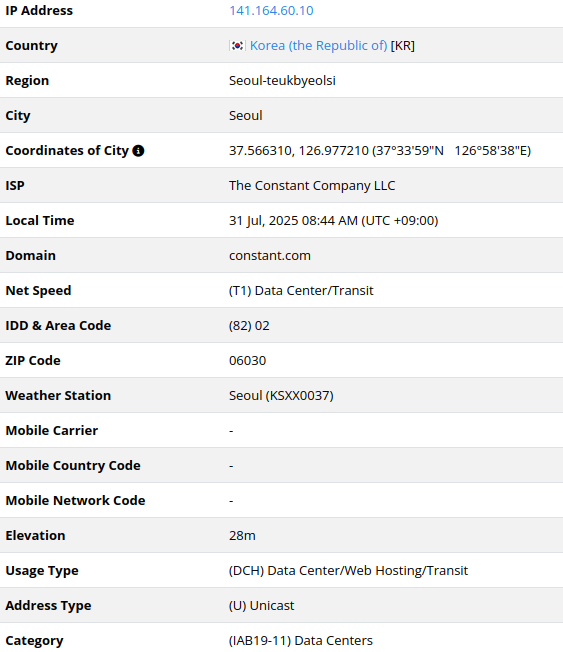
141.164.60[.]10
2025-07-22
IP address exploiting SharePoint vulnerabilities
Resecurity analyzed the exploitation activity over time and mapped it
based on the sources involved, considering geography and ISPs. This
analysis reveals certain patterns, with a dominance of abused cloud
service providers:
|
|
|
|
|
|
|
|
|
(Romania) |
||||
|
|
(US) |
||||
|
|
(Germany) |
||||
|
|
(India) |
||||
|
|
(Hong Kong) |
||||
|
|
(Hong
|
||||
|
|
ISP
(Brazil) |
||||
|
|
Packethub
(US) NordVPN |
||||
|
|
(Netherlands) |
||||
|
|
(Taiwan) |
||||
|
|
(Netherlands) |
||||
|
|
(US) |
||||
|
|
(Japan) |
||||
|
|
(Japan) |
||||
|
|
(US)
CyberGhost VPN |
||||
|
|
(Hong Kong, legal entity in the UK) |
||||
|
|
(UK) NordVPN |
||||
|
|
(South
|
||||
|
|
(South Korea) |
Abuse of Telecommunication Providers and Cloud Services
There is substantial evidence that Chinese cyber threat actors,
including both state-sponsored groups and cybercriminals, have actively
targeted and abused US-based and foreign telecommunication providers.
One of the most prominent examples is the group known as Salt Typhoon
(also referred to as RedMike), which has been implicated in a series of
sophisticated cyberattacks against US telecom infrastructure.
Salt Typhoon’s Campaigns: Salt Typhoon has exploited vulnerabilities in
Cisco edge devices (notably CVE-2023-20198 and CVE-2023-20273) to gain
unauthorized access to telecom networks. These attacks have affected at
least eight US telecom firms, allowing the hackers to access private
communications, including texts and phone conversations of senior US
government officials and political figures. The breaches have been
described as some of the most egregious national security breaches by a
nation-state hacking group in US history.
Exploitation of
Lawful Intercept Systems: Salt Typhoon has also managed to access lawful
intercept systems used by US internet service providers, which are
designed to accommodate law enforcement requests. This access enabled
the group to intercept private communications, further raising national
security concerns.
Broader Campaigns: Chinese state-sponsored
groups have a history of targeting managed service providers (MSPs) and
telecommunications service providers (TSPs) to gain access to sensitive
information, as seen in campaigns like Operation Cloud Hopper.
In the exploitation campaign collectively referred to as “ToolShell”
(CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, CVE-2025-53771),
Chinese actors were also actively leveraging foreign telecommunication
infrastructure through the abuse and misuse of cloud services, resellers
of virtual and dedicated servers, and hosting providers. The industry
should accelerate the implementation of enhanced KYC procedures to
detect suspicious customers who may be linked to nation-state actors
originating from China.
Exploitation Patterns Observed
Payload sizes typically 7000-8000+ bytes
URL-encoded compressed data in CompressedDataTable parameter
Specific User-Agent string: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0)
Content-Type: application/x-www-form-urlencoded
Connection: close header often present
Base64-encoded serialized .NET objects in payload
Response contains machine keys in pipe-delimited format
Secondary requests to deployed spinstall0.aspx files
SharePoint ULS Logs
Monitor SharePoint Unified Logging Service (ULS) logs for:
Category: SharePoint Foundation Web Controls
Level: Unexpected, Error, Critical
Keywords: “ToolPane”, “ExcelDataSet”, “Deserialization”
Process: w3wp.exe
Key indicators in ULS logs:
Unexpected exceptions in ToolPane.aspx processing
Deserialization errors in Microsoft.PerformancePoint components
Memory corruption or process crashes in w3wp.exe
IIS Access Logs
Monitor IIS logs for exploitation patterns:
# Log analysis queries (replace with your SIEM syntax) cs-method="POST" AND cs-uri-stem="/_layouts/15/ToolPane.aspx" cs-method="POST" AND cs-uri-query="DisplayMode=Edit&a=/ToolPane.aspx" cs-bytes > 7000 (typical exploit payload size) cs(User-Agent)="Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0" cs(Referer)="/_layouts/SignOut.aspx" sc-status=200 AND time-taken > 5000 (slow processing indicating deserialization)
Specific IOCs from real attacks:
POST /_layouts/15/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspx Content-Length: 7699 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0 Referer: /_layouts/SignOut.aspx Body contains: MSOTlPn_Uri=http%3A%2F%2F[domain]%2F_controltemplates%2F15%2FAclEditor.ascx Body contains: CompressedDataTable%3D%22H4sIAAAAAAAEANVa23LbSJLt3stEzMzu0%2F6AQs%2B2BJCiu%2BWQ
Network Traffic Analysis
Monitor network traffic for:
Unusual POST request sizes to SharePoint servers
Repeated requests to ToolPane.aspx from single sources
Base64 encoded payloads in HTTP POST bodies
Non-browser User-Agent strings targeting SharePoint
Windows Event Logs
Monitor Windows Event Logs on SharePoint servers:
Event Log: Application
Source: ASP.NET, SharePoint Foundation
Event IDs: 1309, 1310 (application errors)
Event Log: System
Source: Application Error
Process: w3wp.exe crashes
SIEM Detection Rules
Splunk Detection Query:
index=iis source="*iis*" | search cs_method="POST" cs_uri_stem="/_layouts/15/ToolPane.aspx" cs_uri_query="DisplayMode=Edit&a=/ToolPane.aspx" | eval payload_size=tonumber(cs_bytes) | where payload_size > 7000 | search cs_User_Agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0" | stats count by src_ip, cs_uri_stem, payload_size | sort -payload_size
Enhanced Detection for Real Attacks
index=iis | search cs_method="POST" AND cs_uri_stem="/_layouts/15/ToolPane.aspx" | where cs_bytes > 7000 AND cs_bytes < 10000 | search cs_Referer="/_layouts/SignOut.aspx" | eval attack_pattern=if(like(cs_User_Agent, "%Windows NT 10.0; Win64; x64; rv:120.0%"), "CVE-2025-53770", "Other") | where attack_pattern="CVE-2025-53770" | table _time, src_ip, cs_uri_query, cs_bytes, sc_status
Elastic/Kibana Query
{
"query": {
"bool": {
"must": [
{"term": {"http.request.method": "POST"}},
{"term": {"url.path": "/_layouts/15/ToolPane.aspx"}},
{"term": {"url.query": "DisplayMode=Edit&a=/ToolPane.aspx"}},
{"range": {"http.request.bytes": {"gte": 7000, "lte": 10000}}},
{"term": {"user_agent.original": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0"}},
{"term": {"http.request.referrer": "/_layouts/SignOut.aspx"}}
]
}
}
}
Sigma Rule for CVE-2025-53770
title: CVE-2025-53770 SharePoint ExcelDataSet Exploitation
id: cve-2025-53770-sharepoint-exploit
description: Detects exploitation attempts of CVE-2025-53770 SharePoint deserialization vulnerability
references:
-
author: Security Team
date: 2025/07/21
logsource:
category: webserver
product: iis
detection:
selection:
cs-method: 'POST'
cs-uri-stem: '/_layouts/15/ToolPane.aspx'
cs-uri-query: 'DisplayMode=Edit&a=/ToolPane.aspx'
cs-bytes:
- gte: 7000
- lte: 10000
cs-User-Agent: 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0'
cs-Referer: '/_layouts/SignOut.aspx'
condition: selection
falsepositives:
- Legitimate SharePoint administrative activities
level: high
tags:
- attack.initial_access
- attack.t1190
- cve.2025.53770
References
– SharePoint Zero-Days Exploited to Unleash Warlock Ransomware
– Disrupting active exploitation of on-premises SharePoint vulnerabilities
https://www.microsoft.com/en-us/security/blog/2025/07/22/disrupting-active-exploitation-of-on-premis…
– UPDATE: Microsoft Releases Guidance on Exploitation of SharePoint Vulnerabilities
Disclaimer
All third-party product names, logos, and brands
mentioned in this publication are the property of their respective
owners and are for identification purposes only. Use of these names,
logos, and brands does not imply affiliation, endorsement, sponsorship,
or association with the third-party.
link







